Why We Invested in BlueFlag Security

With every technological paradigm shift or evolution in a technology layer, new security considerations emerge—a fundamental way we identify market opportunities as cybersecurity specialist investors. Regarding the latest investment at 1011vc, one we are thrilled to announce today, the critical paradigm in question is the pace and practice of software development today and how it can be enhanced to result in more robust and safer software products.
The Problem
Modern DevOps, cloud-native architectures, and open-source software have transformed application development. However, with its advantages come risks; the speed and complexity have also created many vulnerabilities and a growing attack vector. Gartner estimates that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains. Software supply chain attacks have been some of the most prominent security breaches. Past high-profile attacks include the Solarwinds attack in 2020, the Log4j attack in 2021, and the Okta attacks in 2022. Regulations continue to be issued in the US and EU that shift the burden of secure software delivery toward producers, driving additional needs for enterprises to govern and secure all aspects of the software development lifecycle (SDLC). Additionally, the responsibility of application security is increasingly shifting toward developers, ushering in an era where security tools must be frictionless, developer-focused, and easy to deploy.
We have evaluated many Application Security and DevSecOps startups in the past. And, while we have seen many excellent point solutions, we struggled to find a company we believed would create a platform approach to provide security leaders with complete oversight and governance ability to meet compliance requirements and security standards. When we re-connected with Raj Mallempati and Ken Schneider, long-time friends of the 1011vc family now founding BlueFlag, we immediately resonated with their approach to creating one comprehensive platform to ensure safer application development – through the lens of identity (as Gartner calls it, “the ultimate control surface.”)
The Vision
Raj and Ken set out to create the perfect environment for safe software development and in doing so, they envisioned an identity-first approach to a new vector: developer activity. Just as security teams added identity controls to employee activity, customer access, and partner permissions, Raj and Ken surmised that security teams could further secure the SDLC process by applying an identity layer to developer activities. By extending access management to the SDLC, security teams could understand and permission identities, human and machine, in the software development process.
This control layer could define and enforce policies that determine how and when developers can access code repositories and source code or when they can make changes to code and push it to production. It would also monitor for risky behavior, detect over-permissioned accounts, and enforce least privilege through remediation workflows in the customer’s native incident response or ticketing systems. BlueFlag would provide this visibility and governance at the granular identity level and by team or group, allowing customers to add business context and integrate with their trusted IAM systems. It would reach across the whole SDLC lifecycle, going beyond identity to add critical context on CI/CD pipeline and asset misconfigurations, adherence to relevant compliance frameworks, and the relation to identities at each layer. Critically, at the same time, it would be seamless, easy to use, and wouldn’t slow down developers in any way.
What’s Ahead
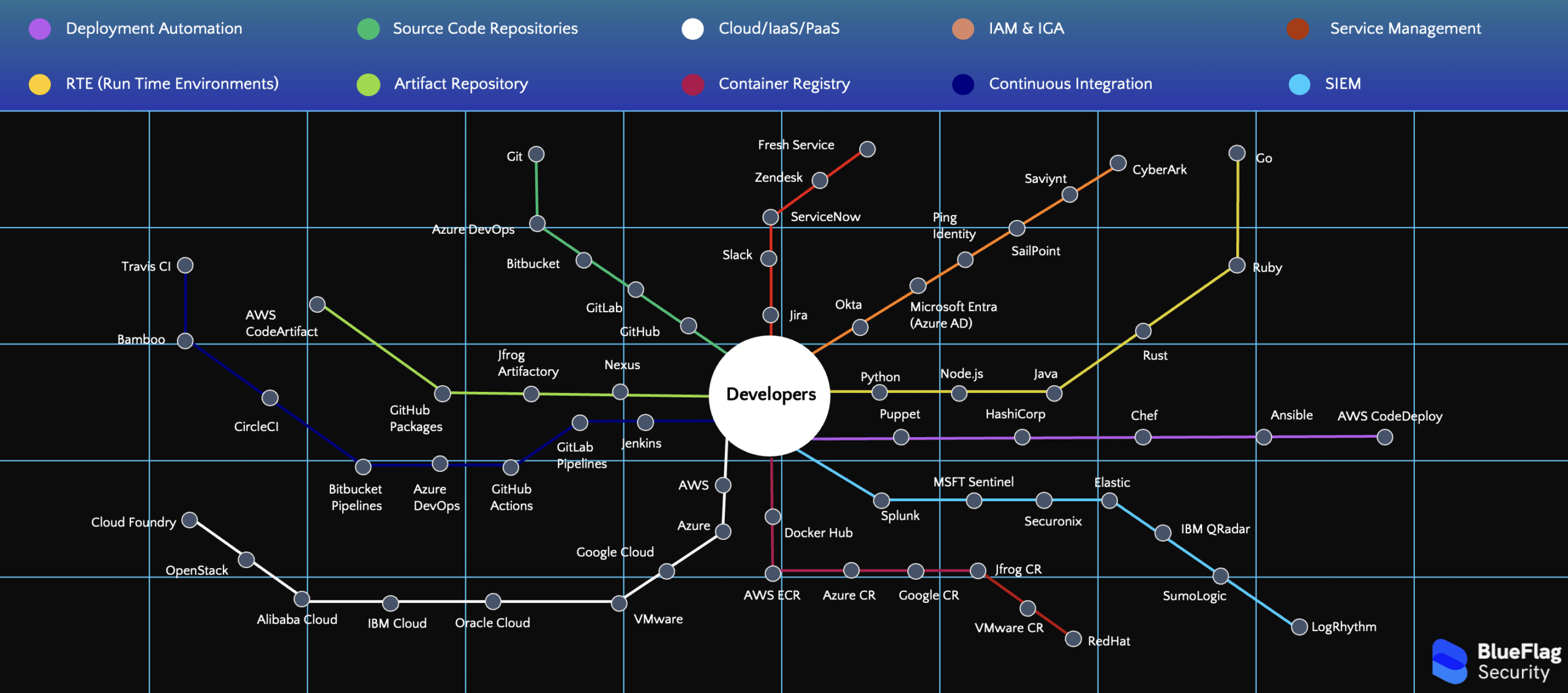
By building this vision over the past months, Raj and Ken have truly created a “pristine ecosystem” in which developers can be productive and effective while security leaders can be confident in security and compliance at the same time. Why will they succeed in the future? Fundamentally, by using identity to secure the disparate environment developers often operate within (including source code repositories), BlueFlag has found a critical opportunity to secure the most critical relationships in digital trust today. The diagram below highlights the surface the company will help secure. As companies grow and the pace of cloud-native application development continues to accelerate, the web of relationships represented will expand exponentially, highlighting why the potential value of BlueFlag’s insight and governance regarding developer lifecycle is so high.
Critically, this is a founding team with the experience and drive to execute such a big and bold objective. Raj and Ken are proven operators with talent and expertise in many domains, including product, technical architecture, and go-to-market. They are laser-focused on getting feedback from users, both dev teams and security teams, to help hone their product and future roadmap to the best place possible. They have assembled a great team, that has a lot of fun working together, including former colleagues from CloudKnox (acquired by Microsoft in 2021) and others with direct experience in this sector.
We are thrilled to be joined in this round by Maverick Ventures & Pier 88. Together we will work to help Raj and Ken realize the full potential of this new way of approaching secure developer SDLC, and in so doing, produce a safer software supply chain that will benefit us all.


